Stay protected. This is the desire of any business, especially now, when, in addition to physical, economic and natural threats, there are also digital threats. In the IT world, as in nature, everything is interconnected: if there are those who create, there are those who destroy. This cycle poses new challenges for businesses: protecting their digital assets.
The amount of assets lost to hacker attacks in 2023 dropped by more than 50% to $1.7 billion, but the frequency of hacks has remained largely unchanged.
Sometimes the end in itself is not to steal money, but to create circumstances that negatively impact businesses. Recently, for example, Fortinet’s cybersecurity subsidiary reported a DDoS attack on a local firm using smart toothbrushes. The DDoS attack was realized thanks to a hole in the software of specific models written in Java. The preliminary damage is millions of euros.
Whether the aim was to cause the company problems or just a test of strength is unknown, but it does not reduce the level of risk to the business.
Protecting Your Business: Pentesters or White Hacking
Imagine discovering weaknesses before attackers do, fixing them quickly, and strengthening your defences in an ever-evolving cyber battlefield.
Penetration testing represents the pinnacle of preventative cybersecurity measures organized by experienced professionals known as ethical hackers or penetration testers.
With surgical precision, these experts replicate real-world cyber threats in a controlled environment, carefully identifying vulnerabilities before attackers can exploit them. Ethical penetration testing is more than just simulation, it offers actionable information to strengthen your digital defences.
Looking at it from a battlefield perspective: penetration testing is not just a process, it is a shield that protects your borders, and organizations and white-hat hackers are the defenders of these processes.
How penetration test works
Most often, testing consists of 5 steps.
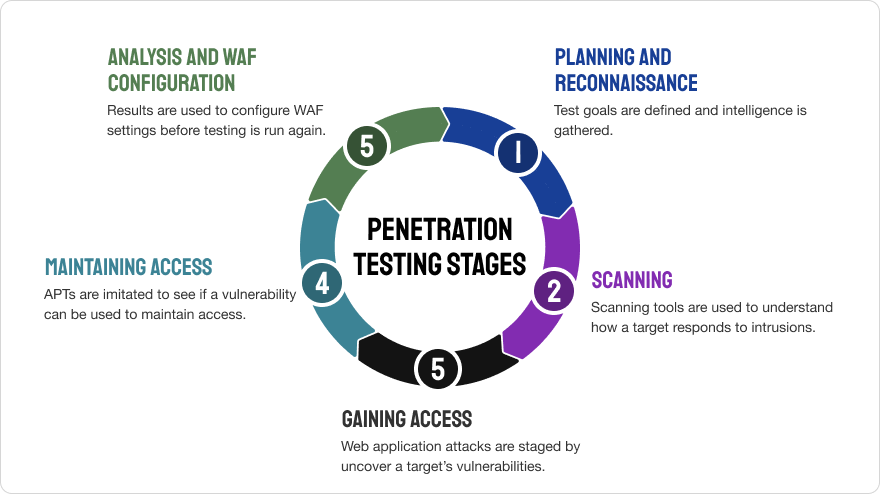
Planning and Exploration
The first stage is the simplest and most obvious – define the scope and goals of testing, systems, methods and the result to be achieved. For this kind of work it is very important not to withhold anything: network and domain names, mail servers, etc. The more materials and data that get into the hands of the test writer, the less risk that a vulnerability will remain somewhere.
Scanning
At this stage, it is important to understand how the application will react to hacking attempts. In a way, it is similar to testing the human immune system. Two types of scanning are actively used:
- Static analysis – reviewing the code and evaluating its response at one time
- Dynamic – analyzing based on the response of the application in a running state
Punching or gaining access
This stage consists of attacking by all available means to find vulnerabilities. Once they are found, a “deep dive” into the system is performed to assess what data and how much data can be extracted through the next hole.
Maintaining access
The results of hacks come in one-time and long-term. This depends not only on the speed of response, but also on the hackers’ ability to leave a discreet gap behind them and pull data through it. In this way, a long-term hack is simulated with the deepest penetration and an assessment of what kind of data can be stolen in this way.
Analysis
The final stage where the results are summarized. Vulnerabilities are assessed, their extent, how long it took to get this or that data. Based on the results, updates are made to the service or application security environment to proactively respond to the threats found.
Challenges and risks
While the benefits of ethical penetration testing are undeniable, overcoming its challenges requires a detailed approach. From finding and retaining the best ethical hackers to determining the scope of testing initiatives to addressing legal and ethical issues, organizations must proceed with caution. However, with strategic planning and following industry best practices, these challenges can be overcome.
Main types and methods
Black Box: Imagine a security consultant acting like a real-world hacker. They have zero knowledge of your internal systems, networks, or applications. Their mission? Break in and find vulnerabilities just like a malicious actor would. This method mimics real-world attacks and is ideal for discovering external vulnerabilities that could be exploited by hackers. However, it can be time-consuming as the consultant starts from scratch.
White Box: Now, imagine giving the consultant the keys to the kingdom. They have complete access to everything: source code, network maps, credentials, and more. This allows them to deep-dive into your systems and identify vulnerabilities in areas like coding errors, security misconfigurations, and weak access controls. White Box testing offers a comprehensive assessment of both internal and external vulnerabilities. However, the sheer volume of data can make it time-intensive and expensive.
Grey Box: This approach strikes a balance between the two. The consultant has partial knowledge, like login information or architectural designs. This speeds up the initial reconnaissance and allows them to focus on high-risk areas. It’s a good choice for simulating insider threats or targeted attacks where the attacker might have some internal access.
How to live with risk
In the face of complex systems and evolving threats, organizations face a critical choice: remain vulnerable or proactively strengthen their defenses. Choosing to engage in ethical hacking isn’t just about decisions, it’s an unwavering commitment to resilience.
Imagine navigating the digital world with confidence, knowing that vulnerabilities will be identified and closed before attackers exploit them. By partnering with ethical hackers, organizations gain this foresight and control, ensuring not only their own protection, but the security of the entire digital ecosystem. Ethical penetration testing is not a guarantee, but a firm promise to create a more secure and sustainable digital future for generations to come.









